
TECH TALK
Insider Tips to Make Your Business Run Faster, Easier and More Profitable
INSIDE THE ISSUE
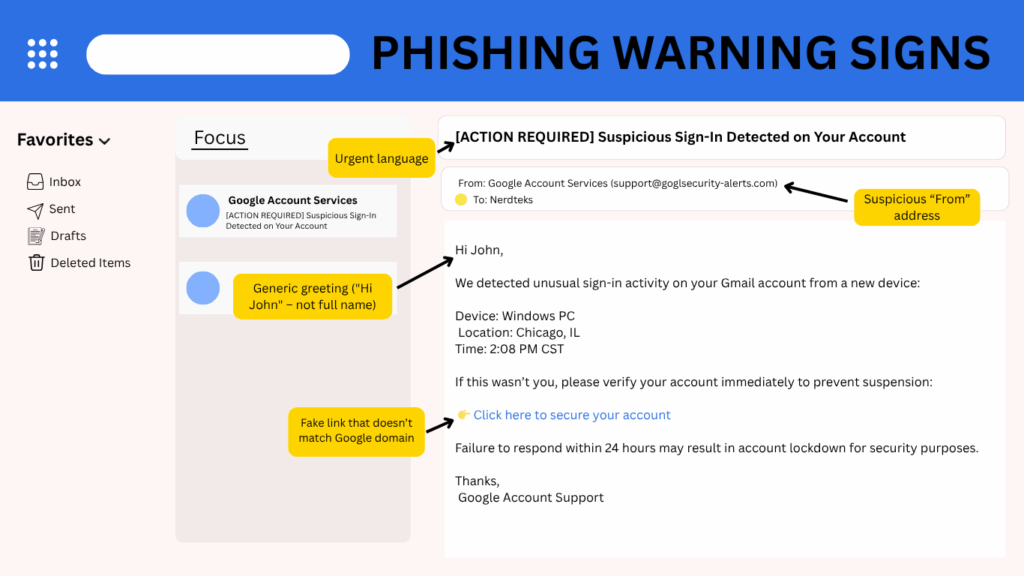
New Gmail Threats in 2025
What Are the New Threats to Gmail in 2025?
7 Unexpected Ways Hackers Can Access Your Accounts
Keep Your Gmail Account Safe
What Are Other Dangers That Users Should Know About?
New Gmail Threats Targeting Users In 2025 (And How To Stay Safe)
Cybercriminals target Gmail a lot because it’s very popular. It also integrates with many other Google services. As AI-powered hacking attacks become more common, it gets harder for people to distinguish between real and fake emails.

What Are the New Threats to Gmail in 2025?
Cyber threats are constantly evolving, and some of the most sophisticated attempts have been aimed at Gmail. One major concern is that Artificial Intelligence (AI) is being used to create scam emails that appear very real. The purpose of these emails is to mimic real ones, making them difficult to spot. AI is also being used to create deepfakes and viruses, which complicates security even further.
Gmail is deeply connected to other Google services. This means if someone gains access to a user’s Gmail account, they might be able to access all of their digital assets. These include:
When hackers use AI in phishing attacks, they can analyze how people communicate. This helps them write emails that look almost exactly like real ones. This level of sophistication has made phishing efforts much more likely to succeed. Now, almost half of all phishing attempts use AI technology.
Gmail continually updates its security, so users need to be adaptable to stay safe. Cyber threats are always changing, and Gmail users must stay vigilant to protect themselves.
What Are Other Dangers That Users Should Know About?
AI-powered hacking isn’t the only new threat that Gmail users should be aware of. More zero- day exploits are being used to attack users. They exploit previously unknown security vulnerabilities in Gmail. This allows them to bypass traditional security measures. Attackers can access accounts without permission before Google can address the issue.
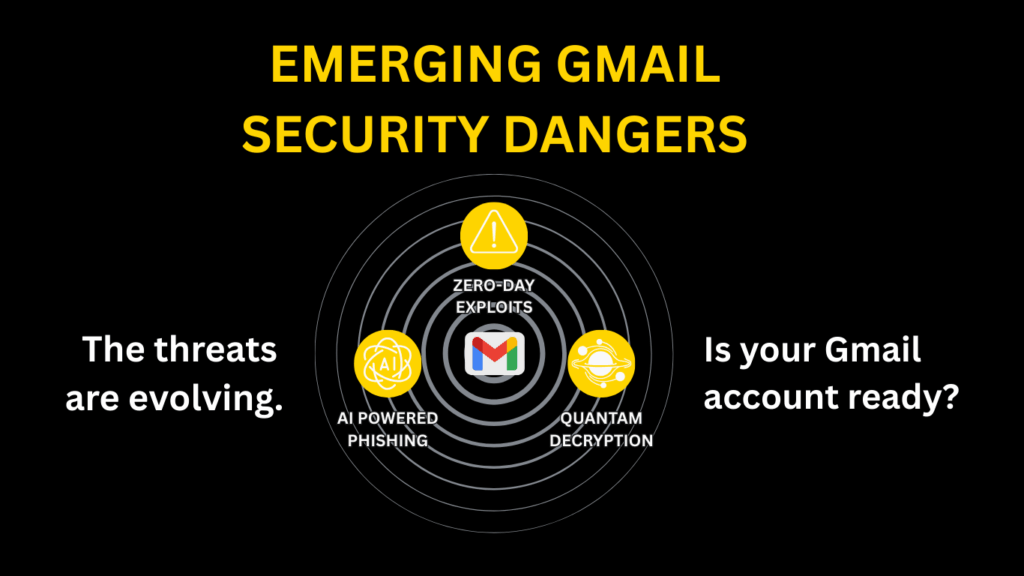
Quantum computing is also a huge threat to current encryption methods. As quantum computing advances, it may become possible to break complex passwords and encryption keys. This could make it easier for hackers to access Gmail accounts. Users can implement strong passwords, enable two-factor authentication, and regularly check account settings for suspicious activity.
Keep Your Gmail Account Safe
Users can protect themselves by staying informed, regularly updating their knowledge, and implementing robust security measures.
Staying up-to-date on the latest security practices and best practices is important to keep your Gmail account safe. In today’s cyber world, it’s crucial for both individuals and businesses to protect their digital assets. Don’t hesitate to reach out if you’re concerned about keeping your Gmail account safe or need more help avoiding these threats. You can count on our team to help you stay safe online as the world of hacking continues to evolve.
7 Unexpected Ways Hackers Can Access Your Accounts

In today’s digital landscape, hackers are constantly evolving, deploying increasingly sophisticated tactics to breach personal and business data. The threats aren’t always obvious — many come disguised as everyday technologies or legitimate communications.
From cookie hijacking and SIM swapping to deepfake scams and AI-powered phishing, cyberattacks are now more deceptive than ever. Here are seven unexpected cyber threats every individual and business should watch out for — and tips on how to defend against them.
1. Cookie Hijacking
Web cookies may seem harmless, but when compromised, they can be used to hijack your active sessions. Attackers can gain access to your accounts — no password required — simply by stealing these small data files.
Defense Tip: Regularly clear cookies and use secure browsers with anti-tracking features.
2. SIM Swapping
In a SIM swap attack, hackers impersonate you to your mobile provider and convince them to transfer your number to a new SIM card. Once they control your number, they can intercept calls, texts, and authentication codes.
Defense Tip: Add a PIN to your mobile account and enable app-based two-factor authentication (2FA) instead of SMS.
3. Deepfake Technology
AI-generated deepfakes can mimic the voice or appearance of someone you trust — like a colleague or family member — tricking you into sharing sensitive information or even transferring money.
Defense Tip: Be skeptical of unusual requests and verify identities through secondary channels.
4. Exploiting Third-Party Apps.
Third-party integrations can expand your productivity — but they also create potential vulnerabilities. If an attacker breaches one of these apps, they could gain access to your entire digital ecosystem.
Defense Tip: Regularly audit third-party apps, revoke unnecessary permissions, and monitor API access.
5. Port-Out Fraud
Port-out fraud is another form of identity theft where your phone number is transferred to a new provider without your knowledge. Once done, attackers can bypass many forms of identity verification.
Defense Tip: Set up account-level locks or alerts with your mobile provider to flag any port-out requests.
6. Keylogging Malware
Keyloggers silently record your keystrokes, capturing login credentials, financial information, and more. These often sneak in through phishing emails or malicious downloads.
Defense Tip: Use antivirus tools with anti-keylogger protection and avoid installing unverified software.
Phishing has gone high-tech. Cybercriminals now use AI to craft emails that are eerily realistic and tailored to the recipient, making them far more convincing than traditional phishing attempts.
Defense Tip: Educate your team on phishing recognition, and use email security tools that scan for AI-generated content.
Stay Ahead of the Threats
Being proactive is key to cybersecurity. At NerdTeks, we help secure your infrastructure using real-time vulnerability scanning, threat detection, and compliance alignment (HIPAA, NIST, PCI DSS). Whether you’re managing M365, on-prem servers, or hybrid environments, we’ve got your back.
Have questions or need a security assessment? Reach out anytime at sales@nerdteks.com your trusted IT security partner.



Latest Posts